Last updated: April 4, 2024
Le Sidejacking, also called session hijacking, is a formidable hacking technique that allows cybercriminals to steal your sensitive information discreetly.
Indeed, with this attack, a hacker can intercept your web session and steal your usernames, passwords, Bank data and other confidential information.
Make no mistake, no one is safe from sidejacking. Whether you are a simple Internet user, a professional or even a large company, your data can be the target of these sneaky attacks.
So, how to protect yourself? Solutions exist to minimize risks and surf safely. In this article, we reveal to you the dangers of sidejacking and deliver to you the keys to protect yourself effectively.
How exactly does sidejacking work?
Sidejacking (or session hijacking) involves intercepting and using insecure session cookies to access users' online accounts.
But what is a cookie?
Well, this is a small text file that a website saves on your computer or your mobile device when you visit it.
These files allow the site to remember your actions and preferences over a period of time.
This way, you don't have to reconfigure them every time you return to the site or navigate from one page to another.
For example, to see the cookies saved on your Chrome web browser, just follow these simple steps:
- Open Chrome and navigate to the site whose cookies you want to view.
- Right-click anywhere on the page.
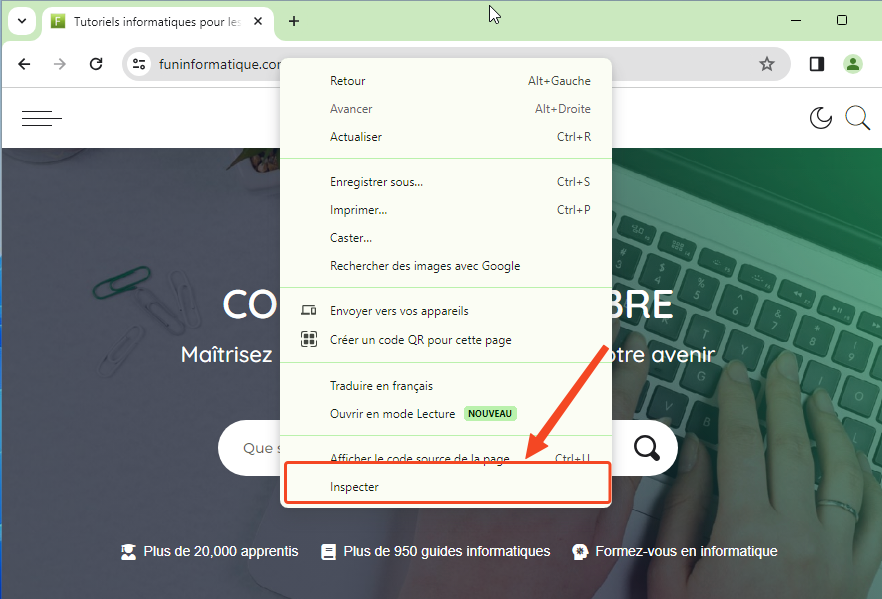
- Select Inspect to open Chrome Developer Tools.
- In the Developer Tools window, find and click the tab Application.
- In the tab Application, sous Storage In the left pane, select Cookies.
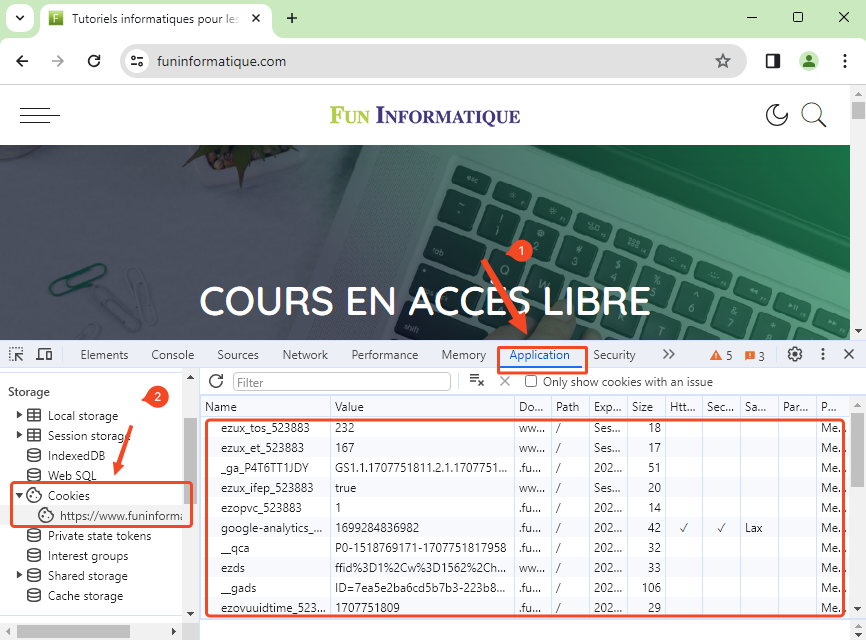
- You will now be able to see the cookies associated with the site you inspected.
How do hackers exploit session cookies?
Hackers take advantage of the fact that many websites transmit session cookies in the clear, without encryption. Among these cookies, some allow websites to log you in automatically when you visit them, without you having to enter your login details each time!
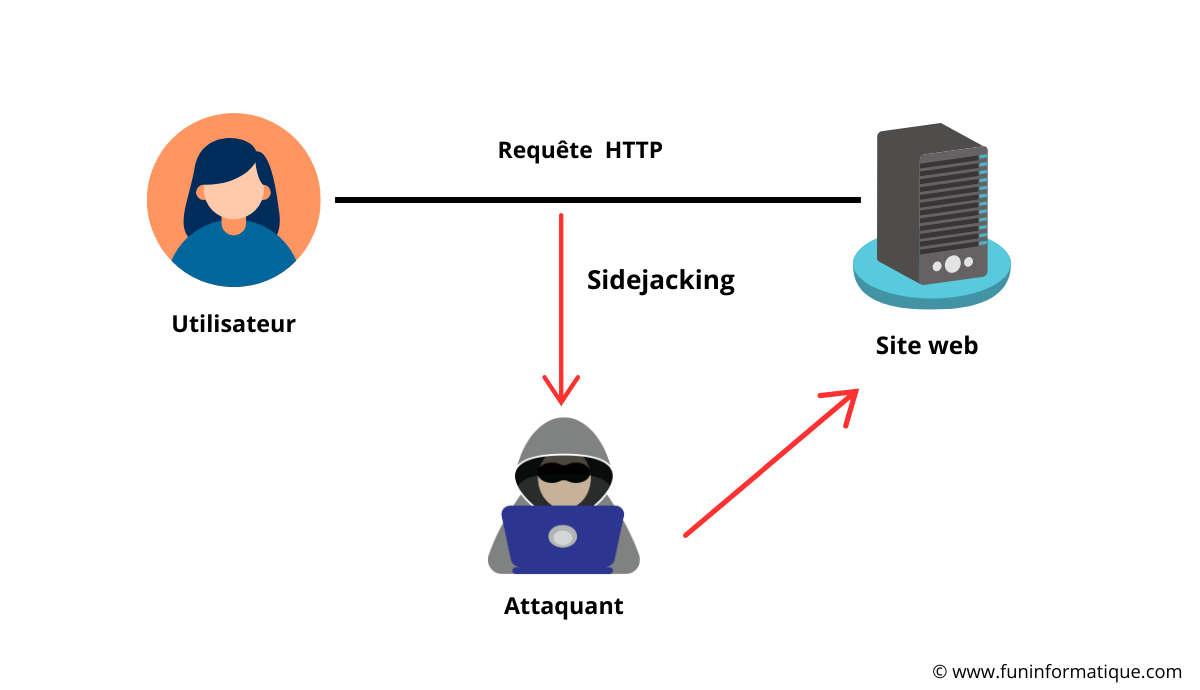
So, getting their hands on these cookies allows the hacker to pretend to be you and access your accounts without a login or password, thus giving them access to your personal information and the ability to take control of your accounts by line.
For more details, read our tutorial: How can a hacker exploit your cookies?
This technique exploits the weakness of insecure and unencrypted communications on the network, particularly on public Wi-Fi networks. HTTP (and not HTTPS) Web sessions are certainly increasingly rare but still exist, it is one of the entry points.
The accesses Poorly secured public WiFi (for example in a restaurant or hotel) are also more vulnerable.
How do hackers capture your cookies?
In a typical side jacking scenario, an attacker could use a network analysis software, or snort, to capture data packets transmitted over a WiFi network public.
By analyzing these packets, the attacker can extract session cookies and use them to access victims' accounts.
Social media sites, email accounts and online banking are prime targets for side jacking attackers.
Hackers use various tools and software to carry out these attacks.
Here are some examples:
- Wireshark : It is a very popular network packet analyzer that allows users to see data transmitted over a network in real time. Hackers can use it to intercept and analyze insecure session cookies.
- Firesheep : It is a browser extension that was created to demonstrate the vulnerabilities of insecure session cookies. It allows session cookies to be intercepted on unsecured Wi-Fi networks and access to user accounts.

- Sniff : It is a collection of tools for network analysis and sniffing attacks. It can be used to capture data packets and retrieve session information.
The different types of hijacking attacks
Side jacking session
In the case of side jacking session, hackers intercept a user's network traffic, usually by monitoring an unsecured WiFi network.
By carefully analyzing this traffic, they can spot unencrypted session cookies exchanged between the user and the website. Once they steal these cookies, they can use them to impersonate the user and access their online accounts without needing their credentials.
Malicious code injection (Cross-site scripting)
In this attack, hackers exploit the XSS flaw of a website by inserting malicious scripts.
Using this method, attackers can, for example, store scripts in the site's database or send them directly to a user through links or forms.
When a user visits an infected page, the script runs in their browser, allowing the hacker to steal sensitive information such as session cookies.
For more details on this attack, see this article: XSS flaw, what is it and how to protect it?
Session fixation
In a session fixation attack, hackers create a valid session ID and then trick the user into using it to log in to a website.
To achieve this, they can, for example, send an email containing a link to a fraudulent login form.
When the user uses this session ID, then hackers can access their online account without any permission.
Guess session IDs
Finally, in the case of session ID prediction, some web servers use predictable algorithms to generate session IDs.
Hackers can capture these credentials and analyze the patterns to predict valid credentials.
This method can be compared to a brute force attack, where hackers test different combinations of credentials.
Man-in-the-browser attack
To carry out this attack, hackers must first infect your computer with malware, often through downloads or infected email attachments.
Once your computer is infected, the malware waits patiently for you to visit targeted websites.
When you transact online, malware can then intervene and modify the transaction data, allowing hackers to access your usernames and passwords.
How to protect yourself from Sidejacking?
To conclude the article, as usual, we will provide you with the best advice to protect yourself from sidejacking.
Always opt for HTTPS connections rather than HTTP
HTTPS is a secure communications protocol that encrypts data transmitted between your web browser and the server. This makes it harder for hackers to intercept your data.
For webmasters, use the Secure flag for session cookies
Secure cookies can only be transmitted over encrypted HTTPS connections. The Secure flag tells the browser to only transmit session cookies over HTTPS connections.
Avoid unsecured public WiFi networks
Unsecured public Wi-Fi networks are particularly vulnerable to sidejacking attacks. If you must use public Wi-Fi, avoid connecting to sensitive sites such as online banking or e-commerce sites.
 Using a VPN encrypts your Internet connection
Using a VPN encrypts your Internet connection
A VPN creates an encrypted tunnel between your device and the VPN server. This makes it harder for hackers to intercept your data.
Enable two-step verification for your sensitive accounts
Two-step verification adds an extra layer of security to your accounts. Even if a hacker manages to obtain your password, they will also need your verification code to log into your account.
Enable HTTPS by default in your browser
Major browsers now offer native support for an HTTPS-only mode.
To enable HTTPS in your browser, here is how to do it depending on your web browser:
- Firefox : Go to Settings > Privacy & Security > Check Enable HTTPS only mode.
- Chrome : Go to Settings > Privacy & Security > Security > Enable Always use secure connections.
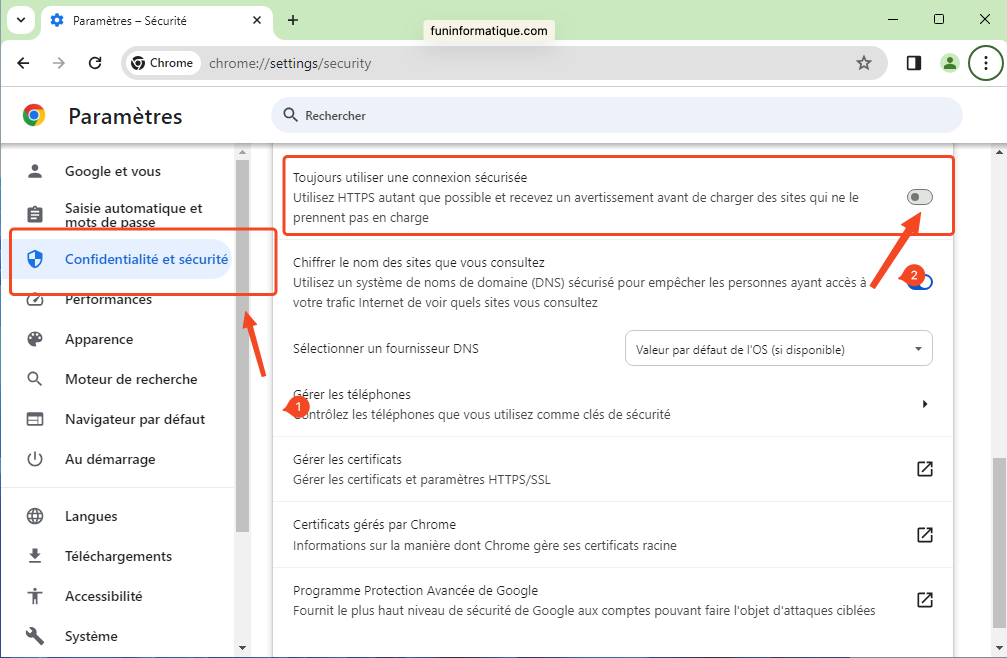
You can type in the address bar:chrome://flags/#https-only-mode-setting. - Edge : Enable automatic HTTPS via
edge://flags/#edge-automatic-https, then in the privacy settings, enable Automatically switch to more secure connections with automatic HTTPS. - Safari : For users of Safari 15 and later on macOS Big Sur or macOS Catalina, HTTPS is enabled by default, with no need to change.
For the more experienced, use your attacker's weapons: Wireshark
Wireshark is a powerful tool that can be used to monitor network traffic and detect possible suspicious activities.
In addition to these tips, here are some other steps you can take to protect yourself from sidejacking:
- Update your web browser and operating system regularly.
- Install an antivirus and a firewall.
- Be careful when clicking on links or opening attachments from unknown people.
- Never grab Your personal information on an unsecured website.






Need help ? Ask your question, FunInformatique will answer you.