Last updated: January 27, 2023
The first tools that allowed system administrators to analyze computer networks and locate a problem precisely were the sniffers.
These tools are also within the reach of hackers who also use them to spy on a network IT and steal the different types of data.
In this article, we will see what is a sniffer, its usefulness, the risks it presents and the services vulnerable to sniffing.
What is a sniffer?
The term sniffer is more popular than other terms such as " protocol analyzer " and " network analyzer ».
A sniffer is a program that captures all the packets circulating on a network and which allows their content to be edited. It can capture any information sent across a local network, and therefore display both the identity of users and their passwords transmitted by any service carrying clear data (not encrypted), such as Telnet, DNS, SMTP, POP3, FTP and HTTP.
If the data is not encrypted and if it passes through the network interface of the machine where the sniffer is running, the latter captures it and offers it for direct reading.
Who uses Sniffers and why?
- LAN / WAN administrators use the sniffer to analyze network traffic and participate in determining where there is a problem on the network.
- A security administrator could use sniffer, strategically placed throughout the network, as an intrusion detection system.
- They are also one of the most common tools that hackers use.

How can you spy on a network with a sniffer?
The vast majority of Internet protocols pass information unencrypted. Thus, when a network user consults their email via the POP or IMAP protocol, or opens a website whose address begins with HTTP, all the information sent or received can be intercepted.
Here are examples that show how a malicious user equipped with a sniffer can spy on a network and collect confidential information from users of a network.
Logins and passwords recovery
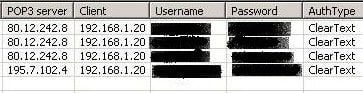
When an average user connects to the POP3 server "a mail server" to check his emails, the hacker retrieves the login / password using a sniffer. It is the same with the connection to a web page which requires authentication.
The images below show how a hacker can to hack a Facebook account and recover the login and password of a user using the Cain & Abel software :
The list of protocols that the Cain & Abel software can sniff:
![]()
Listening to a VoIP communication
A person who uses Skype or other VoIP software to make a phone call may be overheard by a third party. Communication can be easily captured with the sniffer Cain.
The packets are recovered then analyzed before being recorded in audible format, the WAV.
Be careful, some software like Skype now encrypts communications, which makes WAV analysis and recording much more difficult, if not impossible, to obtain an acceptable result.
Read victims' emails
A hacker connected to the same network as you can read your sent emails.
To carry out this attack, all you have to do is install a sniffer allowing the capture of packets according to filtering criteria defined by the user.
In our case, the hacker defines filters so that the sniffer only captures packets whose source or destination port is equal to 25. In principle, any traffic using port 25 is traffic corresponding to e-mails. Since the data in e-mails is usually unencrypted, the hacker can then easily read the content of e-mails passing through the network.
How to protect yourself from a sniffer?
We have seen how easy it is to carry out attacks with sniffers. With little network knowledge, a hacker can easily carry out many of these attacks.
These examples demonstrate vulnerabilities related to network protocols and services, including ARP and unencrypted Internet services.
So the best protection against sniffers is to use encrypted communication protocols, such as SSH (SFTP, scp), SSL (HTTPS or FTPS) (and not plaintext protocols like HTTP, FTP, Telnet).






2 Questions / Answers