Last updated: April 4, 2024
A few days ago I received an email from Google One informing me that my email address and password had been found in a data breach on the dark web.
The leak was from an e-commerce website I had used a few years ago.
I was shocked to learn that my personal information was compromised. Fortunately, thanks to the Google One alert, I was able to act quickly to protect my identity.
In this article I will explain how this leak allowed my Twitter account to be hacked. Next, I'll show you how Dark Web Monitoring works with Google One and how you can use it to receive alerts if your data is leaked.
How did a hacker manage to hack my Twitter account?
In 2016, I signed up for an online strategy game. It was the same address linked to my Twitter account. I admit, I wasn't very active on Twitter and, over time, I even forgot that my account was associated with that old email address.
Until a few days ago, when I received this alert from Google One. My heart jumped. I was both surprised and concerned.
But then, how did my Twitter account get involved in this affair? The same day, by pure coincidence, I tried to access my Twitter account. However, I realized that I couldn't: a message incorrect password was displayed.
While visiting my Twitter profile, I saw announcements from cryptomonnaies and proposals from brokers of all kinds. I quickly realized that I was being hacked.
The turnaround
The hacker had cleverly left my backup email address intact. At first glance, this might seem like negligence, but it was actually a malicious strategy to ensure that I didn't receive any suspicious edit alerts.
Realizing what had happened, I quickly took matters into my own hands. This omission on the hacker's part was his undoing, as it allowed me to reset my password and recover my Twitter account.
How Google One Scanning Works on the Dark Web
After talking about how I got hacked, it's important to talk about a feature offered by Google One.
With Google One, it is possible to create a profile specifically dedicated to monitoring the Dark Web. This means you can actively monitor less accessible parts of the internet, where stolen information is often traded or sold.
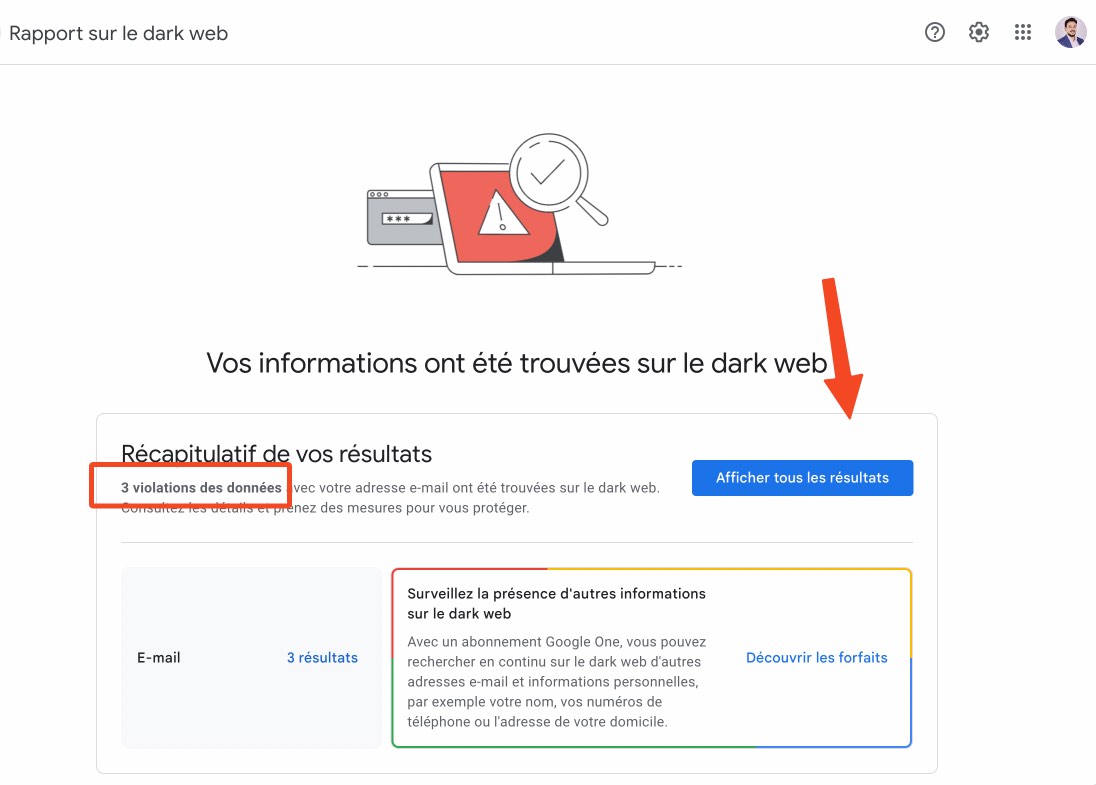
What Google One is looking for can include a fairly wide range of personal information, such as:
- Your name
- Address
- Phone Number
- USERNAME
- Password
What is reassuring is that any information found is displayed in redacted form. This means that your data remains protected; you'll see that a match was found, but without exposing the sensitive details to the open.
How to use Google one to monitor your data leaks on the Dark Web
So, without further ado, here's how you can use Google One to keep an eye on your data leaks on the Dark Web.
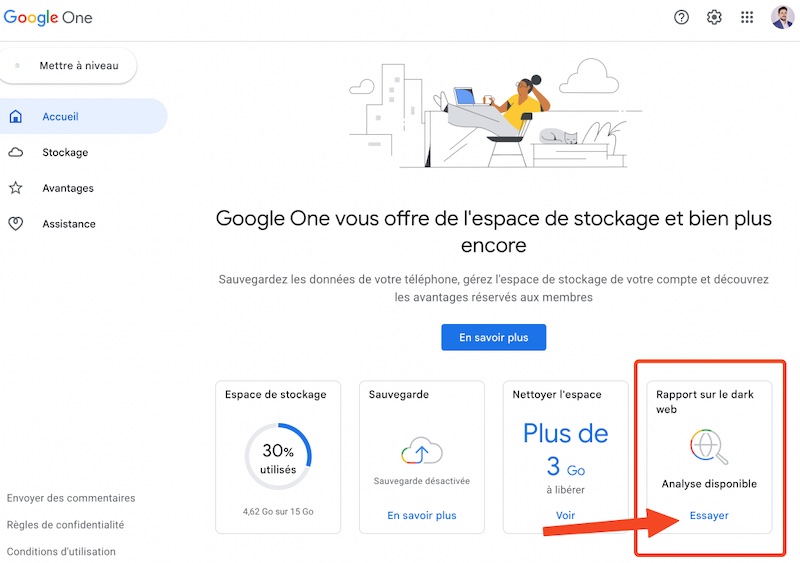
- Sign in to your Google One account.
- Go to the column Dark web report at the bottom right and click Try.
- Then, on the page that appears, click on Analyze.
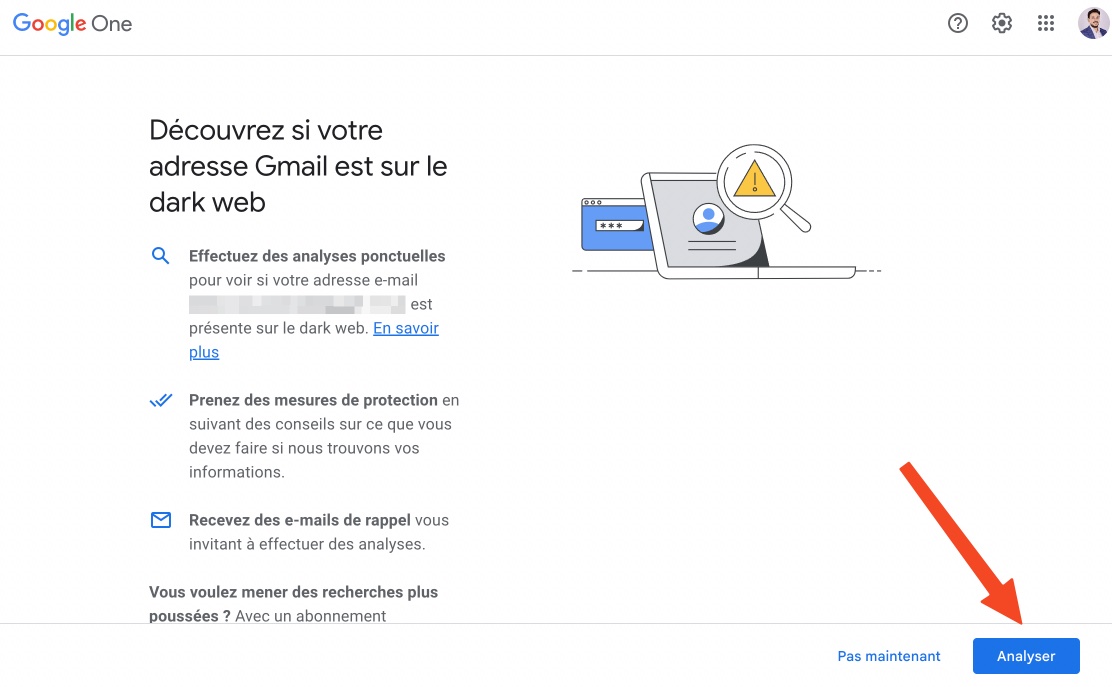
- Wait a few seconds while the scan completes. Finally, you will have all your confidential information that leaked.
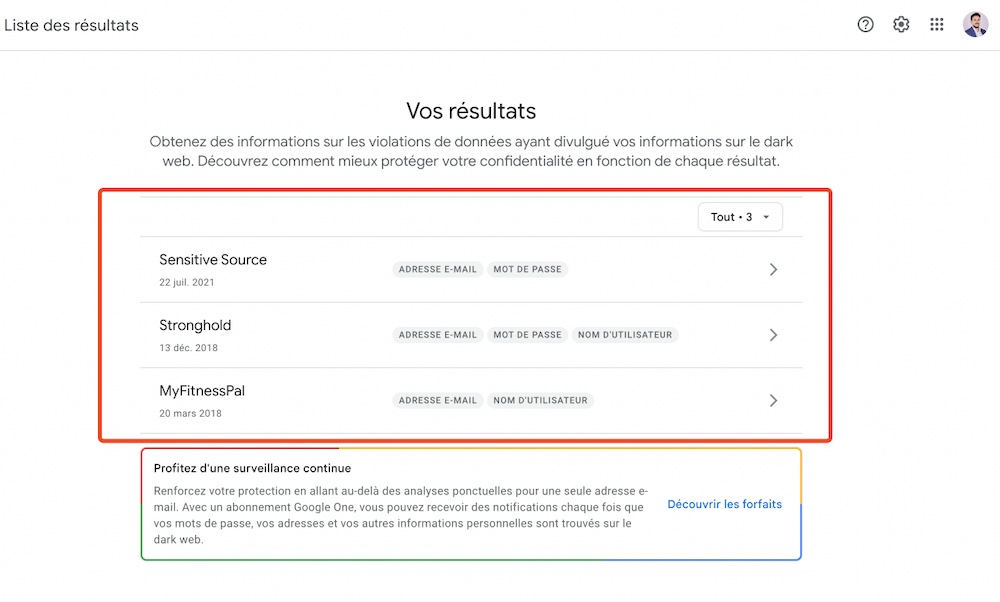
For example, in my case, you will notice that the password and email address of the game Stronghold that I told you about previously were leaked, along with other information associated with different applications that were also exposed.
Tips for protecting your personal data after a leak
Following this mishap, here are the key lessons and measures I adopted to secure my online accounts:
- The first thing I did was check and update the email addresses associated with all my important accounts.
- I enabled two-step verification wherever possible.
- I used a password manager. Not only does this allow me to create strong, unique passwords for each service, but it also prevents me from forgetting or confusing them.
- Finally, and of course, I regularly check information found on the dark web using Google One.






Need help ? Ask your question, FunInformatique will answer you.