In our use of information technology, in particular our e-mails, theopening suspicious documents is unfortunately not such a rare thing, and it can have serious consequences.
In the private domain, if a virus arrives on your machine, it could, for example, collect sensitive data like Bank data, and transfer them to hackers, or simply damage your machine.
For the professional field, suspicious documents can also hide software of the type ransomware who block all the company's files and ask you to pay huge sums to unlock them. So, in this article, we will help you open suspicious documents without taking risks.
Never open suspicious documents directly
We've all had suspicious documents. Generally, they come from emails whose purpose is to scare us by pretending to be the police, for example, or on the contrary to make us hope for profits.
Sometimes it's much more subtle, and in this case it can be a little complicated to see that this document is suspicious. Regardless, if you ever have the slightest doubt about any of these suspicious documents, there is one golden rule.

NEVER OPEN IT! As the adage goes, prevention is better than cure, and so it is better to be overly cautious than risk infection with a virus.
For this, here are three solutions that work very well.
Pass suspicious documents through the Dangerzone software
The first is to use third-party software. The most effective in this area, but also surely the most complete, is called Danger zone. The idea is that he will convert these suspicious documents into secure PDFs.
For those most curious about how this software works, it will create Sandboxes in Docker, all without any network access in order to isolate any viruses that may have been included in your document.
This gives you a document that you can open without any hassle. Where the software is very good is that it allows you not only converts to PDF, but also word processing files and even photos.
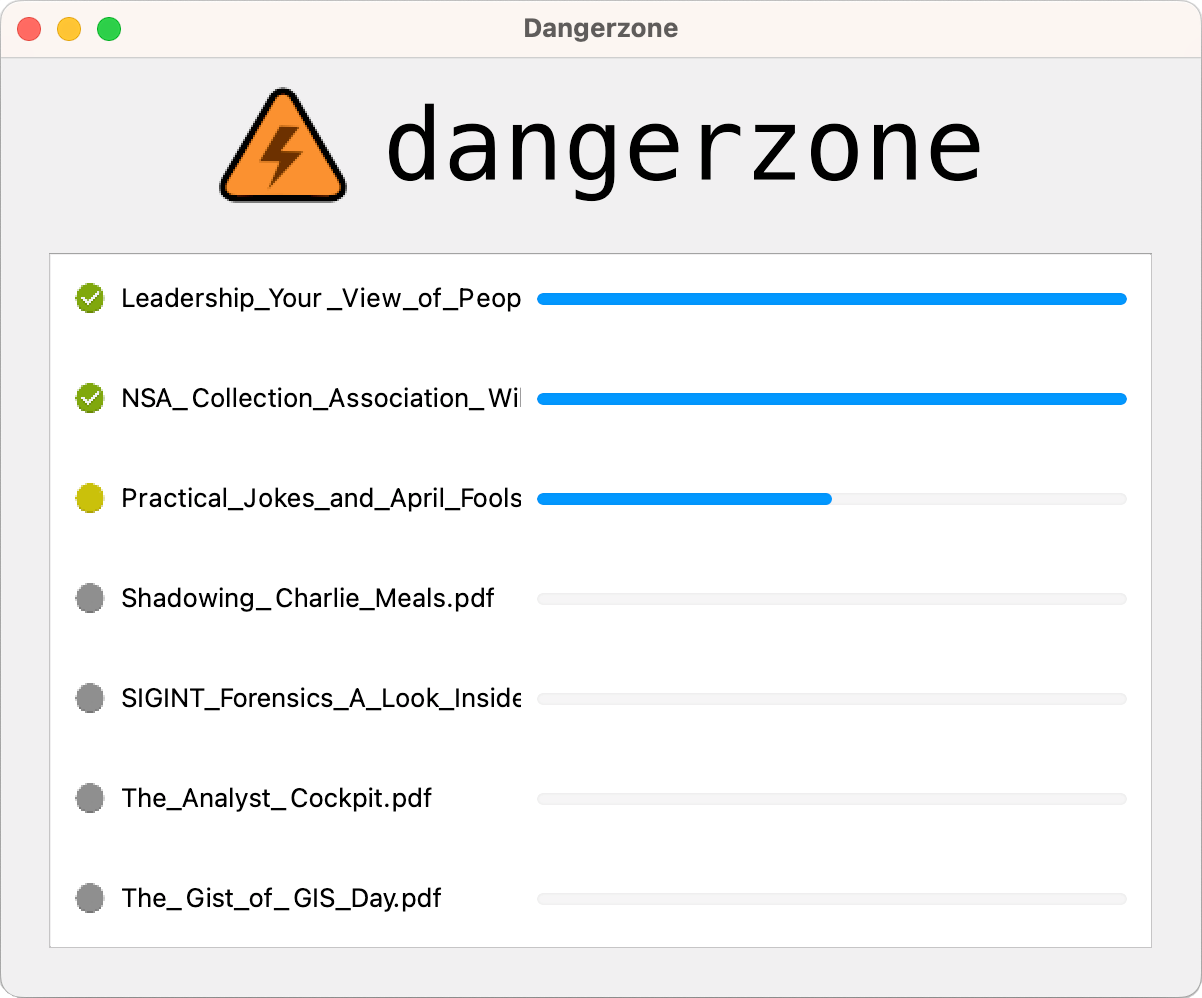
Even better, there is a version of Dangerzone on Linux, on Windows, but also Mac OS. So, no matter your operating system, you will find a version of this software that is compatible!
Dangerzone can convert these types of documents to secure PDFs:
- PDF ( . Pdf )
- Microsoft Word ( .docx, .doc )
- Microsoft Excel ( .xlsx, .xls )
- Microsoft PowerPoint ( .pptx, .ppt )
- ODF text ( .odt )
- ODF spreadsheet ( .ods )
- ODF presentation ( .odp )
- ODF Charts ( .odg )
- JPEG ( .jpg, .jpeg )
- GIF ( . Gif )
- PNG ( . Png )
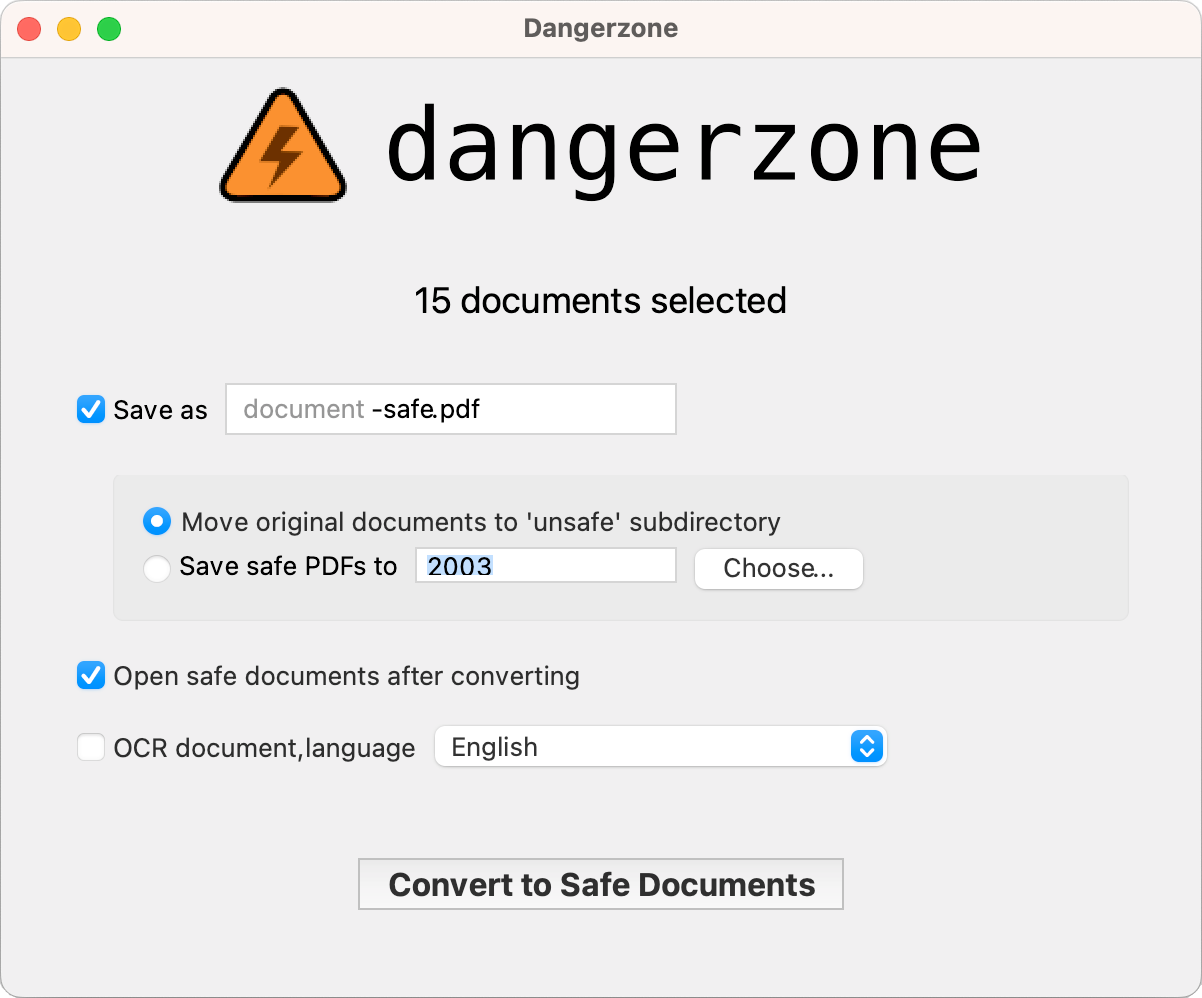
As for using the latter, again, there is nothing very complicated. We have detailed the different steps that you will follow below:
- Download Dangerzone depending on your operating system.
- Launch Dangerzone.
- Download the suspicious document (but don't open it).
- Choose the document on Dangerzone.
- Configure the options.
- Once secured, delete the original document (still without opening it).
- Open the secure version of the document.
Use the Sandbox for users Windows
When we spoke to you in a little more detail about how Dangerzone works, we mentioned theusing a Sandbox. Well know that if you are a user of Windows, you too can use it.
If you are on Linux or Mac OS, unfortunately for you, you will have to find another solution for your suspicious documents. We therefore encourage you to take the first or third option.
If you are on Windows on the other hand, you will be able to use this famous Sandbox Windows which we have just spoken to you about. Be careful though for this to work, you must have a “professional” version of your operating system.
If this is not the case, you will not be able to activate the Sandbox. Finally, be aware that in addition to having the professional version, you must be under Windows 10 or 11 on your machine.
All this being said, let's take a closer look at this Sandbox.
Here's how to activate and use it on your computer:
- Press Win + R to open Run.
- type appwiz.cpl and click OK to open Control Panel.
- In the left panel, click Activate or deactivate features Windows.
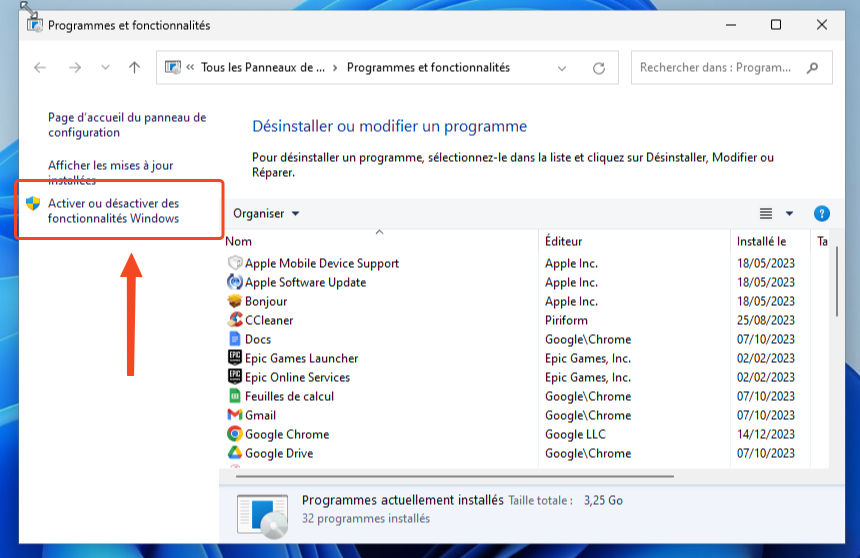
- In the dialog box Activate or deactivate features Windows, scroll down and locate Windows Sandbox.
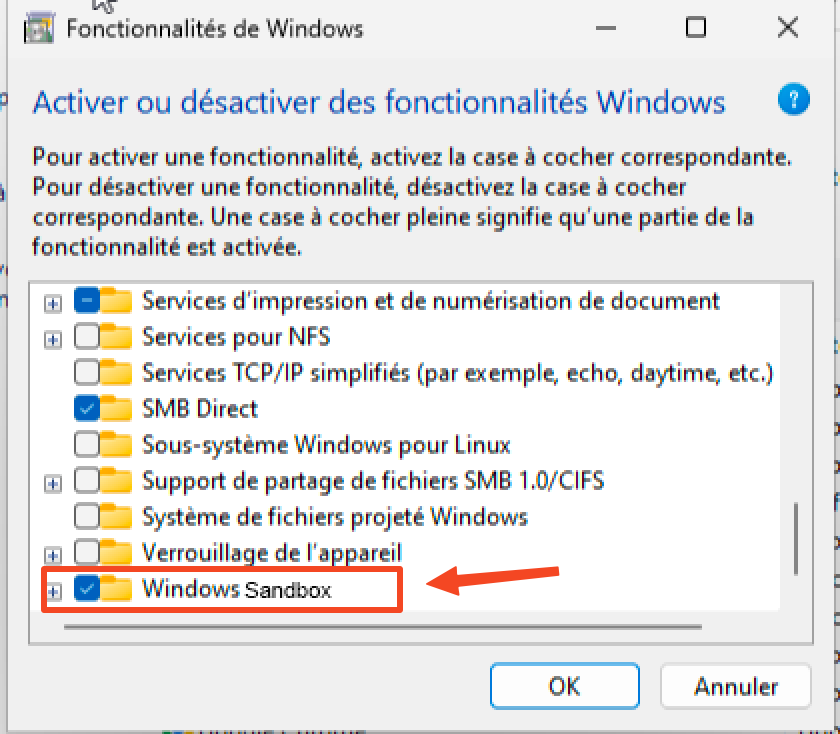
- Check the option Windows Sandbox and click OK.
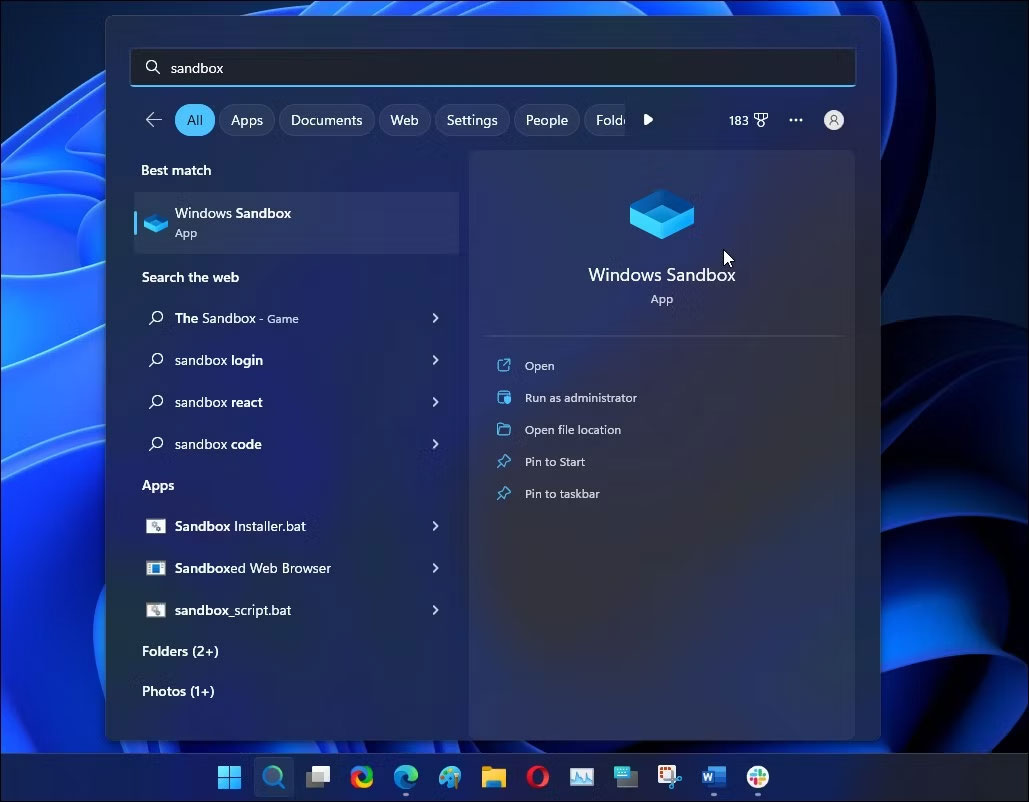
- Restart your PC.
- Go to applications and launch Windows sand box.
- Open the suspicious document via the software.
- Then close Windows sand box.
Go through a virtual machine
Finally, the last technique that we will advise you to manage suspicious documents is to use a virtual machine! In fact, these allow you to protect your basic machine from viruses.
The idea is that if there is contamination, it will take place on the virtual machine which you can quite easily interrupt.
To do this, you must first install virtualization software such as VirtualBox ou VMware on your computer.
Once the software is installed, create a virtual machine and assign it sufficient system resources for its operation. Then simply use it as a dedicated space to open suspicious documents.
In the event of an infection or threat, this will remain confined to the virtual machine, thereby preserving your main system.
Avoid the spread of Malware installed under a Virtual Machine
Be careful though! It is essential to keep in mind that using a virtual machine does not guarantee complete protection and it is always recommended to take a cautious approach and install security solutions such as antiviruses to strengthen the defense of your computer.
Because yes, the most virulent software could still have repercussions on your basic machine. This is rare, but still be careful and keep in mind that it can still happen!
Next, here are a few things to consider:
- VM isolation: Normally, malware in a VM should not infect the real machine.
- File Sharing: Avoid exchanging infected files between the VM and the real machine.
- Network Configuration: Configure the network properly to avoid direct bridges that could facilitate the spread of malware.
- Hypervisor vulnerabilities: Keep the hypervisor up to date to minimize the risk of security breaches.
- Canal Side Attacks: Although rare, these attacks can extract information from the actual machine. Stay vigilant.
Conclusion
That's it, you should now no longer have problems with suspicious documents which are the cause of contaminating your computer with viruses. This obviously does not protect against everything.
However, this helps eliminate a lot of small threats that could bother you. If implementing some of these solutions takes a little time, once you know how to do it, it's immediately faster.
Therefore, as we told you at the start of the article, we strongly encourage you to use one of these three solutions, as soon as you have any doubts about a document that you have just received!






Need help ? Ask your question, FunInformatique will answer you.