Last updated: December 31, 2022
Joomscan Security Scanner is a website audit tool for Joomla. It is written in Perl and it is able to detect more than 550 vulnerabilities like file inclusions, SQL injections, RFI flaws, BIA, XSS flaw, blind SQL injection, protection of directories and others.
Joomscan is intended for IT security professionals and administrators of Joomla sites.
The main features of Joomscan
- Joomla version detection.
- Detection and enumeration of components, plugins and vulnerable modules.
- Posting a defensive note to properly secure your website.
Joomscan installation
Joomscan is available under the Kali Linux distribution. If you have a computer running Windows so I advise you before going any further to install a Linux distribution (like Kali Linux) on a virtual machine. Just download VMware and an image of Kali Linux. here is how to install kali linux on a machine Windows with VMware.
If you have another distribution then you can still download it with the following commands:
cd joomscan
perl joomscan.pl
Find vulnerabilities on a joomla site
After installing Joomscan, the analysis is started using a command line, passing the domain of your site as an argument:
# perl joomscan.pl –u mysite.com

After an analysis, joomscan deduces the version of my joomla portal.
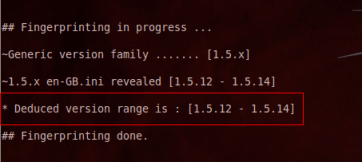
Then it displays the vulnerable components and the description of each flaw that can be easily exploited by a hacker.
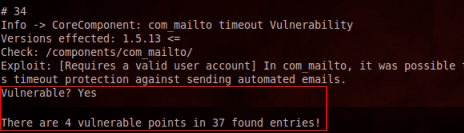
In my case I found 4 flaws on my Joomla site, not bad already.
Otherwise for the correction of Joomla flaws found, it depends on the type of fault. For me, it only took a few updates and the deactivation of a component and everything was back to normal.
You can also display a small defensive note, it is very useful for secure your Joomla site.
There are other optional options for joomscan such as:
-x = if you want use a proxy
-ot = copy the result of the analysis to a txt file
-Oh = copy the result of the analysis to an html web page
Make good use of this tool, remember to make regular backups of your site and take action before it is too late.





4 Questions / Answers