Yesterday a friend told me: “Ahmed, I recently read your article on how to inject a backdoor with a USB key and I also read the article Zeus, King of botnets and I wondered if we can recognize a zombie PC which is part of a hacker's botnet network, knowing that I am sure windows »
To answer this question, I decided to share with you a very effective method for being aware of everything that is happening on your computer.
In fact, when a PC is infected with malware or spyware, it hosts a program that scans the internal disk; either to suck up your contacts to send them to spam databases; or to carry out a relay with other infected machines to constitute a zombie base.
In either case, there are certain signs that shouldn't be overlooked like:
- The fan starts at full speed when the computer is idle.
- The computer takes a long time to shut down.
- Your Friends receive emails with your email address that you did not send.
- Internet access is very slow.
- Opening of ad pop-ups even when your web browser is closed.
How to detect a backdoor on your PC
Please note:: This method that I am showing you does not replace the usual protection methods such as Anti-virus.
To begin, we are going to use free software which will be very useful to us, it is TCPView.
TCPView monitors TCP/IP site activity on your system. Unlike TCP/IP monitoring tools that come with Windows, TCPView shows which process is associated with each TCP/IP address.
Download this tool then unzip it.
No installation is necessary, click on the Tcpview.exe file and the program window opens. TCPView displays network exchanges between your PC and the outside world every second.
The advantage of TCPView over command netstat is that it allows you to close a connection without having to close the corresponding process.
In the case of an infected PC, the remote address is “ exotic ».
Example:
In the screenshot below you can clearly see all open connections on my pc:
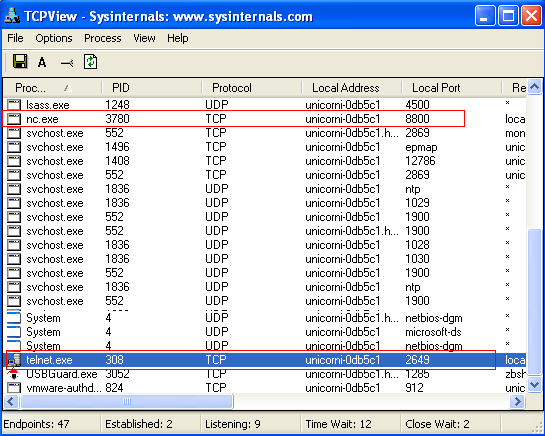
You notice in the picture that there is a Telnet client connected to my computer and also a backdoor cuts Net cat.
TCPView will be able to block this backdoor with one click and identify the location of the program using it to get rid of it.





13 Questions / Answers