WPScan is a vulnerability scanner for WordPress, written in ruby. It is capable of finding vulnerabilities present on a WordPress website, listing the plugins used and giving you the associated security flaws. You can also brute force the administration interface.
It is intended for both security professionals and administrators of WordPress sites.
The main features of WPscan
- Enumeration of users,
- multithreaded brute force password cracking,
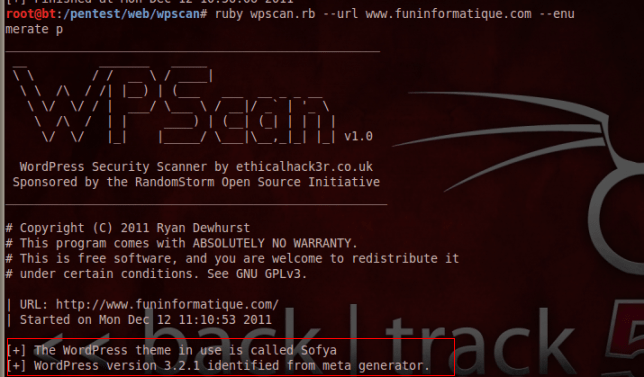
- detection of the WordPress version,
- detection and enumeration of vulnerable plugins.
Installing WPscan
WPscan only works under Linux, if you have a computer running Windows I advise you to use a virtual machine running Kali Linux. Just download VMware and an image of Kali Linux. WPScan is already pre-installed on it. And here how to install kali linux on a machine Windows with VMware.
Otherwise to install it on another distribution, see this page: https://github.com/wpscanteam/wpscan
How to use WPscan?
After the installation we are going to get down to business, most interesting part !
Easy to use:
To know the version of WordPress and the name of the theme used, open a terminal as root and type:
List users:
To list all users who have access to the blog, based on the author of the articles.
List vulnerable plugins
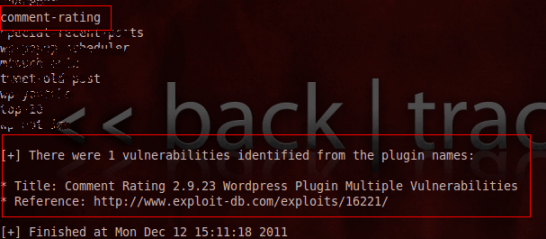
To list the plugins used on a site and display the related security vulnerabilities, run the following command:
You can see on the image that wpscan detected a vulnerable plugin (comment-rating) with a link to the SQL injection type flaw, this flaw can be exploited to have full control of the given database FunInformatique . Don't worry, I've disabled it.
Crack administrator password
To get the administrator password, we will use brute force on the administration interface.
For that, there is no doubt that we will need what is called a dictionary. In the case of a bruteforce attack, the dictionary presents the list of possibilities that the generator will try to use to break into the remote system. In summary, this is the list of tested passwords.
Under Kali Linux, by default, a list exists but you are free to add other words. The dictionary present by default under Kali Linux is located under:
/pentest/passwords/wordlists/darkc0de.lst
If you have a different distribution of Kali Linux, You can download the dictionary here and there.
In short, here is the command that calls on the dictionary in order to have the password of the wordpress administrator:
/pentest/passwords/wordlists/darkc0de.lst –username admin
Protect your WordPress site
To counter all of these techniques, you need to remove the readme.html at the root of WordPress, keep WordPress and plugins up to date, and use a long password with lots of different characters. We can also install a plugin like User Locker which allows you to limit the number of authentication attempts.






Hello, I can't find the wordlisr darckc0de.lst even though I'm under kali 🙁
Can you give me a download link with it please 🙂
Thank you for this article. Just for information, there is now an updated version that you can install with the following commands in BackTrack:
“apt-get update && apt-get upgrade”
The thank you box
Thanks for the information ! 😉
You have to install all the gems. Type the following commands:
sudo gem install --user-install mime-types
sudo gem install --user-install typhoeus
sudo gem install --user-install xml-simple
After installation, the program will work fine 🙂
Morning ,
when i type this command ruby ./wpscan.rb –url an error msg will be displayed
root@bt:/pentest/web/wpscan-1.0# ruby ./wpscan.rb –url
ERROR: Missing ruby gem. Please see README file.
#
____________________________________________________
__ _______ _____
/ / __ / ____|
/ / /| |__) | (___ ___ __ _ _ __
/ / / | ___/ ___ / __|/ _` | '_
/ / | | ____) | (__| (_| | | | |
/ / |_| |_____/ ___|__,_|_| |_| v1.0
WordPress Security Scanner by ethicalhack3r.co.uk
Sponsored by the RandomStorm Open Source Initiative
_____________________________________________________
#Copyright (C) 2011 Ryan Dewhurst
# This program comes with ABSOLUTELY NO WARRANTY.
# This is free software, and you are welcome to redistribute it
# under certain conditions. See GNU GPLv3.
ERROR: The remote website seems to be down
Help me what I have to do!!!
Thanks in advance