The developers of the Tor project have published Wednesday on the official blog of the project a post accusing the FBI of paying $1 million to theCarnegie Mellon University to take advantage of their work to attack the Tor network and get the real IP address of servers and network users.
The case began in 2014 when the Carnegie Mellon University presentation was canceled at the last minute during the Balck Hat conference. The university planned to explain how to break Tor's anonymity.
This is why on Wednesday, the director of Tor, Roger Dingledine, accused the university of having monetized its discoveries with the FBI for the sum of 1 million dollars.
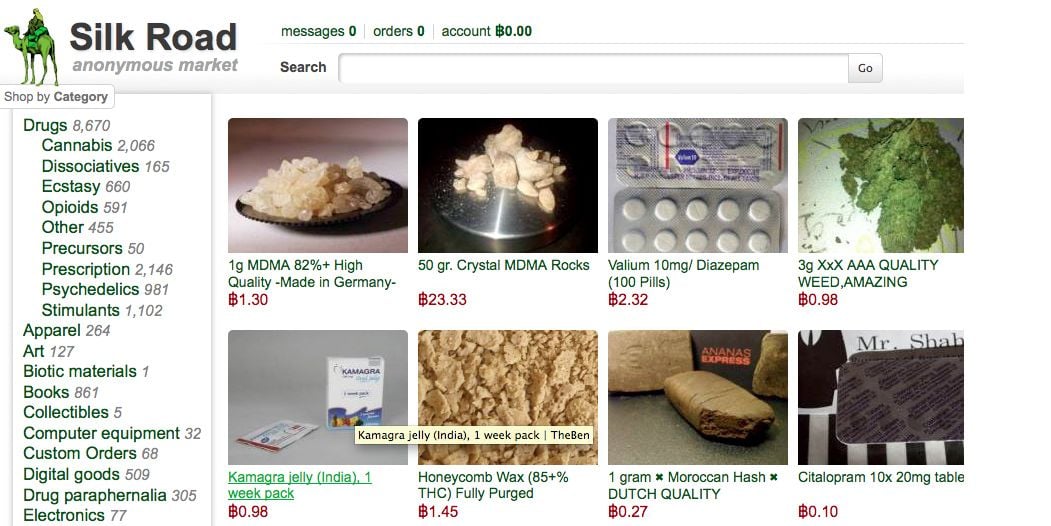
The main objective of the FBI has been to identify the real IP addresses and then to locate the main administrators of the SilK Road 2.0 portal, a marketplace " darknet »Marketing all kinds of banned products, foremost drugs. The investigation resulted in the arrest last January of Brian Richard Farrell identified as the main admin of the site. Many analysts wondered how the federal investigative agency had seen the members of this platform identified so quickly: we now have the answer.
It is clear that governments do not like the idea of a world where it is possible to discuss or exchange files completely anonymously, as the Tor project proposes. However, for the Tor team, this is an attack that goes "against civil liberties", considering that there is little chance that the FBI would have obtained a warrant to act in this way. .
However, if this maneuver were confirmed, it would not be the first of this type. In July 2014, Russia announced that it would offer nearly 4 million rubles – 85.000 euros – to anyone capable of decrypting data sent via the Tor network.





Need help ? Ask your question, FunInformatique will answer you.