webshag is a web server audit tool which works on different operating systems. It is written in Python and it offers, among other things, detect web directory tree, detect server version, scan URLs. It is indeed particularly specialized in the discovery of directories and "hidden" files thanks to several methods.
It also has a file name and directory name fuzzer, which can be useful for retrieving information hidden by an unwary webmaster. Webshag works under two interfaces (Graphics and CLI).
Installing webshag
Under linux:
wget http://www.scrt.ch/outils/webshag/ws110.tar.gz tar zxvf ws110.tar.gz chmod + x setup.linux.py ./setup.linux.py
Under Windows:
Download the installer from the following address: http://www.scrt.ch/ then launch the executable file.
How to use webshag?
webshag requires the following in order to be fully functional:
• Python 2.5 / 2.6
• wxPython 2.8.9.0 graphics library or higher
• The Nmap tool
After installing Webshag, launch the application in graphical mode as well, you will have an interface with four options:
-
PSCAN
Allows you to scan the ports of a website, this module uses Nmap. It will not work if Nmap is not installed.
-
INFO
Info allows you to obtain several pieces of information on the analyzed domain.
-
SPIDER
The spider allows you to scan a website entirely, each link, folder or email address is noted. It is possible to specify the folder in which the scan will start. By default, the root is chosen.
-
USCAN
USCAN allows URL scanning. The skip field allows you to enter parameters in order to ignore certain results.
-
FUZZ
The FUZZ module allows you to find hidden files or pages. It can be used in two distinct modes of operation: list mode and generator mode. List mode is based on three lists of directory names, files and common extension. Based on this, it exhaustively tries the different lists on the target.
Example of use
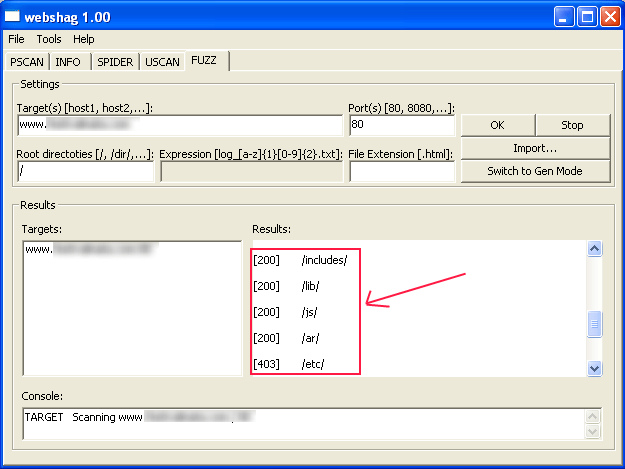
To use the fuzz module, enter the URL you want to analyze then click “OK”. After a few minutes, webshag retrieves the path of the directories hosted on the server with the access type.
For example in this analysis, I was able to find important folders without protection by htacess (like the include and lib folder).





Need help ? Ask your question, FunInformatique will answer you.