Most developers, when shown an XSS flaw with a JavaScript pop-up like "hack" or "hello", do not impress them... and they respond that JavaScript is secure, and that it runs on the client side.
So since I don't have time to code with JavaScript to show you that the XSS flaw is dangerous, I'm going to demonstrate it with the Beef tool, a Web 2.0 operating framework coded in PHP & JavaScript.
Beef is a powerful professional security tool, unlike other security tools, beef focuses on exploiting vulnerabilities on the browser (client) side to assess the security level of a target. Thanks to Beef, and its xss attack vector, it is possible to transform a victim into a zombie.
What can we do with beef?
- Information retrieval
- Theft of cookies (obviously)
- Keylogger
- List of sites / domains visited
- Browser fingerprint (OS, plugins, etc.)
- Webcam!
Architecture Beef
 When a user runs BeEF, two components are opened: the user interface and the communication server (CRC). These two elements are the basic components of Beef.
When a user runs BeEF, two components are opened: the user interface and the communication server (CRC). These two elements are the basic components of Beef.
User interface
This is the beef usage control interface. From there, a user can view victims who are online and offline, run exploits against them, and see the results.
Communications Server
The Communication Server (CS) is the component that communicates via HTTP with infected browsers.
Installation
Beef is available on Linux with the Kali Linux distribution. If you have a computer running Windows so I advise you before going any further to install a Linux distribution (like Kali Linux) on a virtual machine. Just download VMware and an image of Kali Linux. Beef is already pre-installed on it. Here is how to install kali linux on a machine Windows with VMware.
However you can install beef on Windows, for this see: http://code.google.com/p/beef/wiki/Windowsinstall
To install it on another Linux or OSX distribution - see: http://code.google.com/p/beef/wiki/Install
How to use Beef?
To start, launch the beef server in Backtrack. To do this, go to the menu:
Application -> backtrack-> Application -> Exploitation tools -> Social Engineering Tools -> Beef XSS Framwork-> Beef
The server will start in a few seconds then you will have a window with information on the links used for the web interface as well as the script that you must inject into vulnerable pages.
In the example above, you can see, there are multiple network interfaces. You can now access the administration interface (web interface) using these URLs.
In my case, the administration interface is: http://192.168.230.128:3000/ui/panel and the script to inject is: http://192.168.230.128:3000/hook.js
After launching the admin page, you will have an authentication page. Log in to the Beef server using the default credentials (beef/beef).
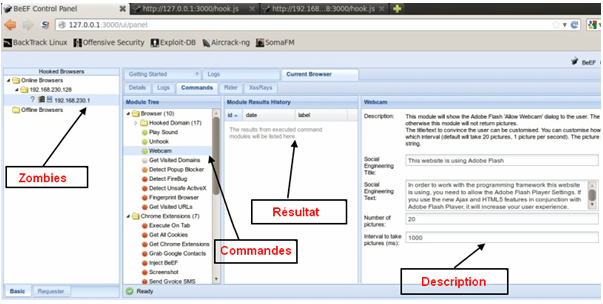
Once connected, you will have a page divided into 4 parts:
- Zombie part: this is where your connected victims are
- Command part: in this part contains a number of commands that can be executed on the target with a colored indicator about their, relative safety. this is the most powerful part of Beef framework.
- Result party: the results of the executed commands will be listed here.
- Party description: here you will have the description of each order.
It now remains to inject the hook.js into a vulnerable forum or simply a web application that contains a XSS flaw.
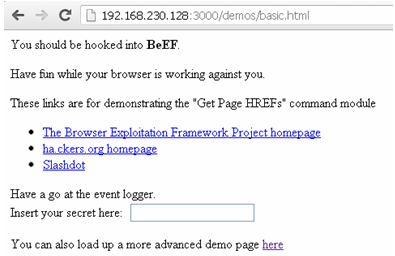
However you can test beef locally using the beef demo page: http://127.0.0.1:3000/demos/basic.html
After the browser infection, you should see a target added to the left of the administration panel.
Finally, select this browser to display information on the target, so you can launch commands to have the last sites visited or to place a keylogger or to start the target's camera.
How to protect yourself?
- Updating browsers and plugins is the first rule!
- Install a firewall on your machine
- Install an Anti XSS on your browser such as “Noscript”. It only allows the execution of JavaScript scripts on trusted domains of your choice. It prevents the exploitation of XSS or CSRF vulnerabilities without loss of functionality.
Conclusion
Beef is an easy to use and very practical tool. Thanks to beef, advanced XSS attacks become easy to perform.
I hope I was able to convince you that the impact of an XSS flaw is terrible and that with a tool like beef, you can transform a simple XSS flaw into a very dangerous vulnerability.
And before I forget… Consider sharing this article by clicking on the social network buttons. It will give me great pleasure! 🙂








I still don't understand the use of beef...
What is this tool for? to infect your own browser? if not, how to inject the hook.js page (which was created on our pc), on the victim's site, even with an XSS flaw and all the stuff we can't (in practice) on a remote site.
Finally I hope I am wrong so that you explain to me in more detail the operation of this tool and the injection of the script into a vulnerable site.
Thank you very much.
Moreover, if you did it yourself without Beef, you would just have to inject a script via the XSS flaw so that this script would be executed discreetly when the user arrives on the page.
Even a simple alert("Hello world!"); will display a popup in the user. Then you can have fun making 50 million popups appear too. It all depends on the type of attack you want to perform 😉
I have a question about beef how to use it online (with a domain name)