DVWA (Damn Vulnerable Web App) is a damn vulnerable web application that is written in PHP / MySql. It's lightweight, easy to use, and full of loopholes to exploit.
DVWA is intended for both security professionals and people wishing to train or want to learn more about web attacks, to test attack techniques in a legal environment.
The main objectives of DVWA
- Learn to identify the vulnerabilities of websites and web applications,
- Test operating and intrusion techniques,
- Learn correction methods to better secure systems.
Web vulnerabilities available in the DVWA application
- Attack by brute force
- Command execution via shell_exec in PHP
- CSRF attacks
- Include fault
- SQL Injection attacks
- Upload flaw
- XSS attacks
Installing Damn Vulnerable Web App
First of all, download the application on Sourceforge, then place the Dvwa folder in your WAMP or XAM or Esayphp web server.
Launch the application on localhost http://127.0.0.1/dvwa/index.php. An installer will allow you to install it in a few clicks.
The login of the application is: admin and the password: Password
To install the database, simply click on setup in the main menu, then click on “Create / Reset Database”.
Practice some attacks on DVWA
The DVWA app contains three difficulty levels: Easy, Medium and Hard.
I recommend that you choose the easy level to start, so as not to get discouraged. Of course, you can move on to the next levels later, but it's best to start smart.
In exploiting a flaw, you will need certain human qualities to be successful: patience, perseverance and discretion. This is a stage where you will have to make the best use of your computer skills, and I am weighing my words. 🙂
Note: To change the difficulty level, click on “DVWA Security” and choose the level you need.
XSS DVWA attack
In order to familiarize ourselves and train with the tool, we will start by carrying out a type attack Permanent XSS.
For that, we will choose “XSS stored” in the menu on the right. A nice form with two fields is then displayed. Normally, the detection of the presence of an XSS flaw can be done by entering a javascript code in a form field or in a URL.
So we type the following line in the message field of our form:
alert('FunInformatique')
If a dialog box appears, it can be concluded that the web application is susceptible to XSS attacks. This script will run each time you visit this page.
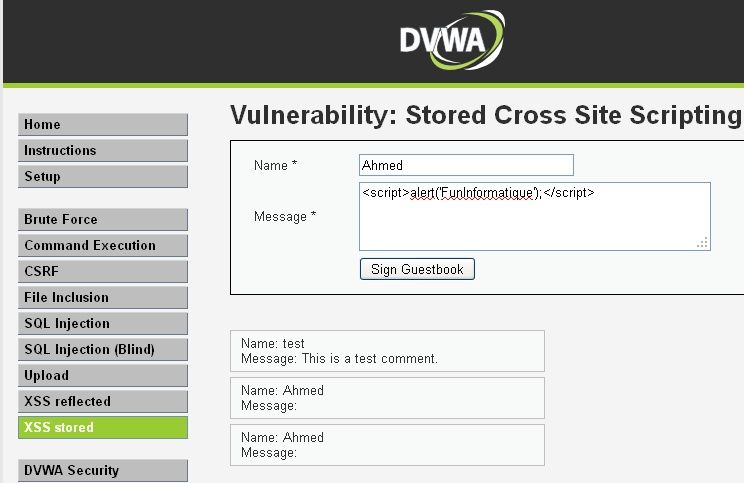
Now all that remains is for you to exploit this flaw with more useful JavaScript code and if you don't have time to code a JavaScript script, use BeEF, an XSS Exploitation Framework.
You should know that in the easy level, security is completely absent in the application.
Upload attack on DVWA
In this part, we will move on to the exploit of the upload flaw (easy level). To do this, we click on “Upload” in the right menu.
The upload flaw is a flaw allowing you to upload files with an unauthorized extension (for example a php code).
To exploit it, we will try to uplode a PHP Web Shell (like C99 or R57) on the server which will give us control of the server.
To do this, click on browse, select your PHP shell and validate
The file is uploded with sucked. You still have to run the shell located in: http: // localhost / dvwa / hackable / uploads /
You can have fun locally with other types of faults in the different levels. Train well and test your penetration testing skills legally. This gives you the opportunity to show what you can do. 😉
And if you're stuck in a test, don't hesitate to let us know in a comment. 🙂







Bonjour.
Thank you for helping us.
Can you let us know the 12 vulnerabilities in DVWA?
Hello Amada,
To exploit all 12 vulnerabilities in DVWA, watch this playlist: https://youtube.com/playlist?list=PLHJCYe4-CQx6H3QhpNTFwTJrEkr9rP45T
thank you for this application but I realize it is not currently available on sourceforge through your link.
so how can i get it?
Very (too) limited
exceptional thank you!
Thank you for this fantastic app...
Thanks for sharing, I've been practicing with this for a few days.
I struggled a bit with the upload fault (whether low or medium level (not tried the hard one, I admit) because apparently there is a weight limit and the shell type c99 or c100 are quite large. I so I uploaded a vulgar .php just to show that we could bypass 'the protection'.
I haven't tried all the categories yet but it seems super interesting!