You may not know this, but to take possession of a computer, hackers almost always use a technique called RunPE. This technique involves taking a legitimate process and replacing it with malware directly in memory.
Your machine Windows is thus deceived and treats the malware as a legitimate process. The antivirus therefore has no idea that the explorer is no longer a nice information program but has transformed into a kind of virus.
This technique is widely used today by hackers. RunPE Detector is an analysis tool that takes care of spot and eliminate these suspicious processes with a simple scan of your computer.
Eliminate malicious processes
Download the RunPE Detector program. Unpack the archive and run it as administrator (right click on the icon). You will then see all the processes running in the background on your machine. Then do Run Scan. The tool will compare the fingerprints of these processes with “known” fingerprints.
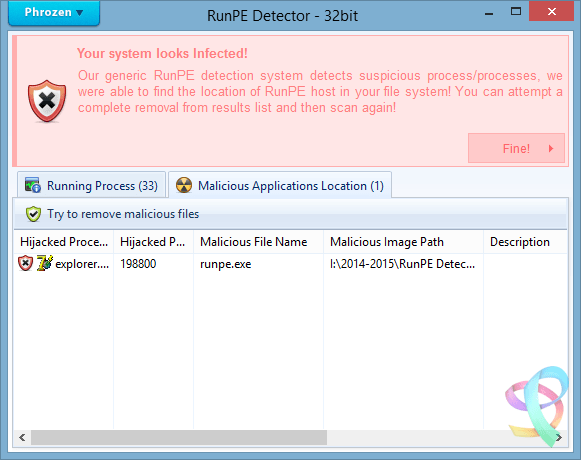
In this example, process # 198800 is suspect. He is named explorer.exe, but it does not have the expected footprint. It is in fact DarkComet who usurped the identity of the explorer Windows! Clicking on Finish! You can delete it...





Yes it's true
I made a video tutorial on my Youtube channel: Bis-Tutos